Cyber Security in the Remote Work Era: Protecting San Marcos, TX Businesses from Digital Threats
Staying Ahead of Cyber Threats in a Changing Work Environment

In today's digital age, remote work has become a staple for many businesses in San Marcos and beyond. At HCS Technical Services, we understand the benefits of telecommuting - from increased flexibility for employees to reduced office costs for employers. Studies even show a 56% reduction in unproductive time when working from home compared to the office.
However, as your trusted IT partner in San Marcos, TX, we want to highlight an important aspect of remote work: cybersecurity. With about 63% of businesses experiencing data breaches due to remote employees, it's crucial to address these risks head-on.
Don't worry - you don't have to sacrifice the perks of remote work for security. Let's explore some key cybersecurity risks associated with remote work and how HCS Technical Services can help you mitigate them.
Remote Work Risks & Mitigation Strategies
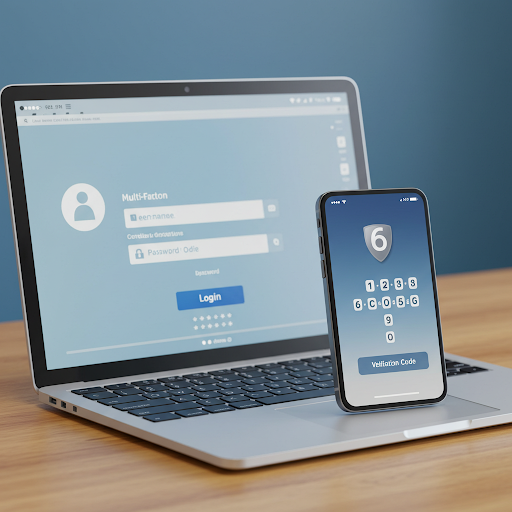
1. Weak Passwords and Lack of Multi-Factor Authentication
Risk: Remote workers often access company systems from various devices, making weak or reused passwords a significant threat.
Solution: HCS Technical Services can help implement robust password policies and set up multi-factor authentication (MFA) systems. We can also deploy advanced access management solutions to enhance your security.
2. Unsecured Wi-Fi Networks
Risk: Public hotspots and unsecured home networks can expose your sensitive data to hackers.
Solution: Our team can set up and configure Virtual Private Networks (VPNs) for your remote staff, ensuring encrypted connections even on untrusted networks.
3. Phishing Attacks
Risk: Remote workers are particularly vulnerable to deceptive emails and messages aimed at stealing credentials or spreading malware.
Solution: HCS Technical Services offers comprehensive security awareness training, teaching your team to identify and avoid phishing attempts. We can also implement advanced email filtering systems.
4. Insecure Home Network Devices
Risk: Internet of Things (IoT) devices can introduce vulnerabilities to home networks used for work.
Solution: We can guide your team on securing home networks and IoT devices. For a more robust approach, we can implement endpoint device management solutions like Microsoft Intune.
5. Lack of Security Updates
Risk: Outdated software and devices are prime targets for cybercriminals.
Solution: HCS Technical Services can manage and automate your update processes, ensuring all devices and software stay current with the latest security patches.
6. Data Backup and Recovery
Risk: Data loss or corruption can be devastating for remote workers and businesses alike.
Solution: We offer secure cloud backup solutions and can implement comprehensive data recovery plans tailored to your business needs.
7. Insufficient Employee Training
Risk: Lack of cybersecurity awareness leaves employees vulnerable to various threats.
Solution: Our expert team provides engaging and effective cybersecurity training sessions, covering everything from basic password hygiene to recognizing sophisticated phishing attempts.
Partner with HCS Technical Services for Secure Remote Work
At HCS Technical Services, we're committed to helping businesses in San Marcos, TX, and the surrounding areas embrace the benefits of remote work without compromising on security. Our tailored solutions address the unique challenges of your remote workforce, ensuring that your team can work flexibly and securely.
Don't let cybersecurity concerns hold your business back. Contact HCS Technical Services today, and let's work together to create a secure remote work environment that empowers your team and protects your valuable data.
Call us now to schedule a consultation and take the first step towards a more secure remote work setup!
HCS Technical Services