Don't Let Informal Policies Put Your Business at Risk
December 12, 2024
The Importance of Formal IT Policies in Small Businesses

Many small businesses make the mistake of skipping formal policies, relying on informal guidelines and verbal instructions to manage their operations. However, this approach can lead to confusion, security breaches, and even lawsuits.
The Importance of IT Policies
IT policies are a crucial part of your company's security and technology management. They provide clear guidelines for employees on how to use technology, handle data, and maintain security. Without these policies, your business is vulnerable to cyber threats, data breaches, and other security risks.
Do You Have These Essential IT Policies in Place?
1. Password
Security Policy
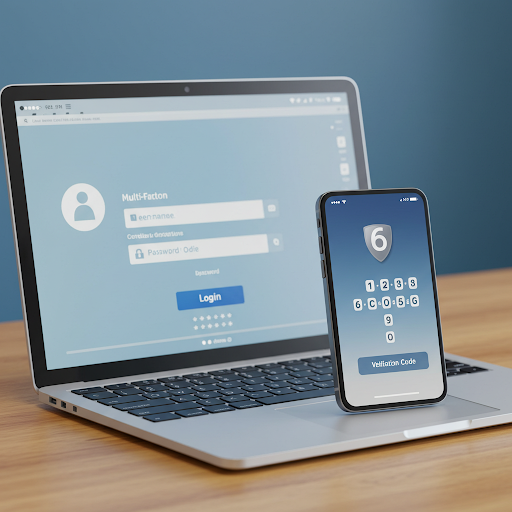
A password security policy outlines the guidelines for creating, storing, and managing passwords. This policy should include:
- Password length and complexity requirements
- Password storage and management guidelines
- Multi-factor authentication requirements
- Password change frequency
2. Acceptable Use Policy (AUP)
The AUP is an overarching policy that governs the use of technology and data within your organization. This policy should include:
- Device security guidelines
- Data storage and handling procedures
- Restrictions on personal use of company devices
- Encryption requirements
3. Cloud & App
Use Policy
This policy outlines the guidelines for using cloud applications and services within your organization. This policy should include:
- Approved cloud applications and services
- Restrictions on unauthorized cloud use
- Procedures for requesting new cloud applications
4. Bring Your Own Device (BYOD) Policy
A BYOD policy outlines the guidelines for using personal devices for work purposes. This policy should include:
- Security requirements for personal devices
- Compensation guidelines for personal device use
- Endpoint management app requirements
5. Wi-Fi Use Policy
This policy outlines the guidelines for using public Wi-Fi and company Wi-Fi networks. This policy should include:
- Safe connection guidelines
- VPN requirements
- Restrictions on public Wi-Fi use
6. Social Media Use Policy
A social media use policy outlines the guidelines for using social media within your organization. This policy should include:
- Restrictions on personal social media use
- Guidelines for posting about the company
- "Safe selfie zones" and facility restrictions
Get Help Improving Your IT Policy Documentation & Security
Our team can help your organization address IT policy deficiencies and security issues. Contact us today to schedule a consultation and get started on improving your IT security.
HCS Technical Services
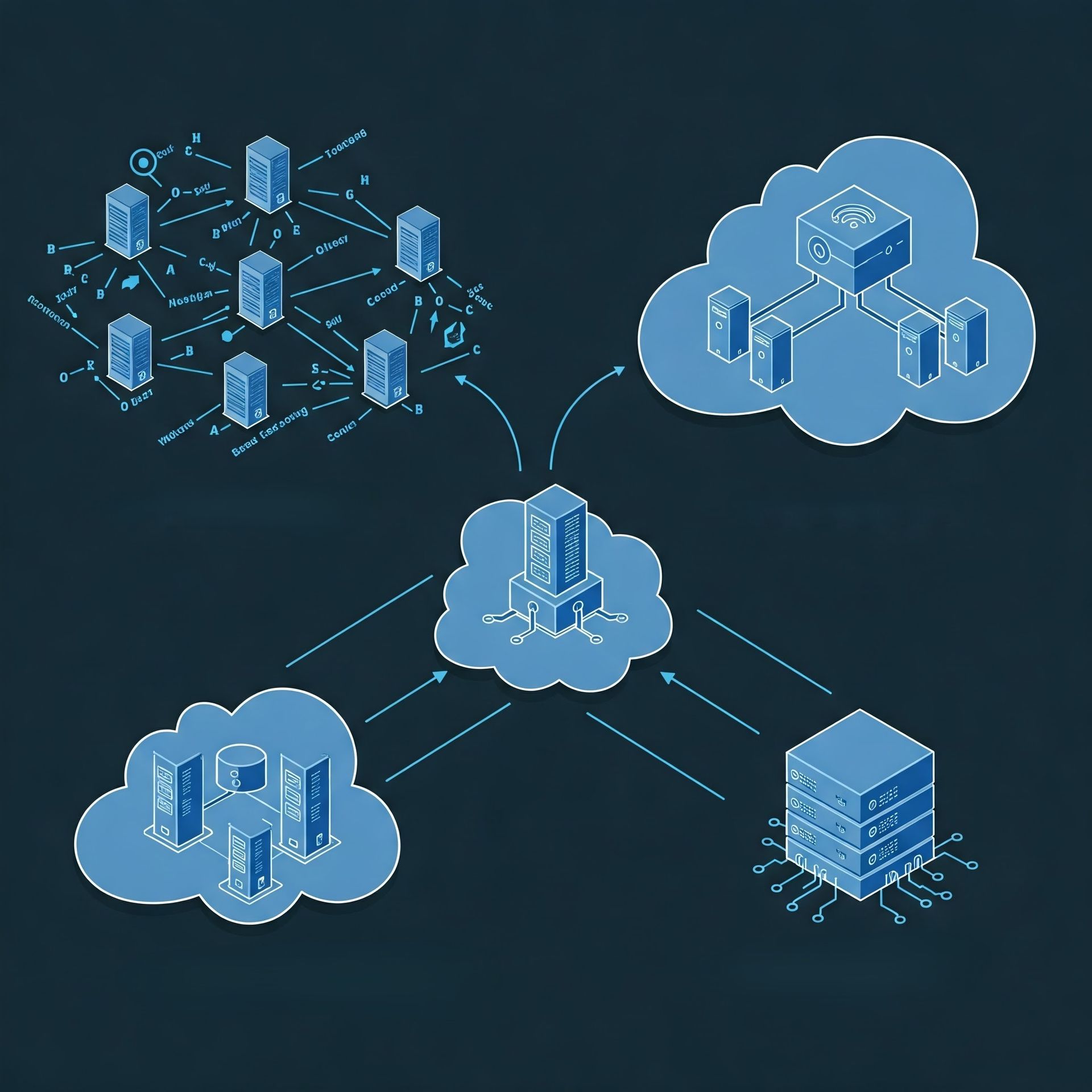
The advent of cloud computing has revolutionized the way businesses handle their IT needs. With several types of cloud models available, choosing the right one for your business can be crucial for operational efficiency and cost management. Cloud models generally fall into three categories: public, private, and hybrid. Each model offers distinct advantages and challenges, and the choice among them typically depends on a business's specific requirements, budget, and objectives. Public clouds are managed by third-party providers and offer scalable resources over the internet, making them appealing for businesses looking for cost-effective solutions with broad accessibility. Private clouds, on the other hand, offer dedicated environments, either on-site or off-site, ideal for businesses needing enhanced security and performance control. Hybrid clouds combine elements of both public and private clouds, allowing greater flexibility by enabling data and application movement between environments. For businesses in San Marcos, Austin, Wimberley, and New Braunfels, choosing the right cloud model involves assessing factors such as data sensitivity, compliance requirements, and IT infrastructure capabilities. Understanding these cloud models can significantly aid in leveraging their benefits, optimizing resource allocation, and ensuring seamless business operations.
In the digital age, misinformation and disinformation have emerged as significant challenges. These are defined as false or misleading information. Misinformation is shared without harmful intent, whereas disinformation is deliberately deceptive. The proliferation of online platforms and social media channels has accelerated the spread of both, impacting public opinion and decision-making processes. Disinformation campaigns can have far-reaching consequences, influencing elections, public health responses, and societal trust. Traditional media channels have lost the monopoly on information dissemination, making it easier for bad actors to spread false narratives. This creates a complex information environment where distinguishing between factual and fraudulent content is difficult. For governments, businesses, and individuals, addressing this issue is imperative. The challenge lies not only in identifying and curbing these falsehoods but also in understanding their origin and impact on public discourse.

Mobile applications have become an integral part of our lives. We use them to browse the internet, network, communicate, and much more. But they open us up to risks caused by fraudsters who may steal information or damage our phones. According to 2024 data from Asee, over 75% of published apps have at least one security vulnerability. This means that 3 out of every 4 your favorite apps could be risky to use. It’s important to be cautious while downloading and maintaining apps. Here are ten simple tips that can help keep your mobile apps secure. Why Is Mobile App Security Important? Not only do 75% of apps risk our security, but business apps are three times more likely to leak log-in information. These risks also include even the most popular apps. Those with over 5 million downloads still have at least one security flaw. Using mobile apps is not always safe. There are many ways for hackers and criminals to steal your data. This can happen because of your internet connection, app permissions, and more. Next, we’ll cover ten essential security tips to keep your data safe when using mobile apps. Top 10 Security Tips For Mobile App Users Mobile apps can be dangerous, but there are ways to reduce these risks. If you’re careful about where you download apps, the permissions you allow, the internet connection you use, and more, you can keep your data as safe as possible. Here are the top ten security tips for mobile app users: 1. Only download from official stores The first step of mobile app security is choosing safe apps. Some apps are not secure, even when they look legit. It’s important to be aware of the source before you click download. Always download your apps from the App Store or Google Play. These stores check apps to make sure they're safe. Don't download from random websites. They might have fake apps that can hurt your phone. 2. Check app ratings and reviews Before you download an app, see what other people are saying about it. If lots of people like it and say it's safe, it is probably fine . But if people are saying it has problems, perhaps you don't want to install it. 3. Read app permissions When you find an app you want to download, stop and do research first. If you download a fake app by mistake, your device may be attacked. It can open you up to malware, ransomware, and more threats. Apps frequently request permission to access certain parts of your phone. Maybe they want to know your location or use your camera. Consider whether they really need that information. If an app requests access to too much, do not install it. 4. Update your phone’s operating system Keep the software on your phone up to date. New updates frequently patch security vulnerabilities. This makes it more difficult for the bad guys to hack into your phone. 5. Use strong passwords We use apps for many day-to-day tasks like sending emails, storing files, and sharing on social media. If an app is hacked, your personal information can be stolen. Passwords protect your apps. Make sure your password is difficult to guess. Use letters, numbers, and symbols. Do not use the same password for all apps. That way, if a person guesses one password, he or she cannot access all your apps. 6. Enable two-factor authentication Two-factor authentication means an additional step in order to log in. It can send a code to your phone or email. This will make it way harder for bad people to get into your accounts. 7. Beware of public Wi-Fi Public Wi-Fi is never a safe space. There may be bad guys watching what you do online. Never use public Wi-Fi on important apps. Wait until you're on a safe network, like the apps for banking. 8. Log out of apps not in use Log out of apps whenever you're done using them. This is even more important when the apps hold personal information, such as banking or email apps. In case someone steals your phone, it's much harder for them to access your apps. 9. Update your apps Developers of applications usually fix security issues in updates. Keep updating your apps whenever newer versions get released. It will help in safeguarding your information. 10. Use security features Lots of apps have additional security features. These may include fingerprint locks or face recognition. Switch these on if you can, as they can help stop other people using your apps. Even with these security tips, it’s important to take other measures to protect your data. Be sure to follow our tips on safe downloads and data protection in addition. Stay Safe While Using Mobile Apps It's not hard to stay safe with mobile apps. Just be careful and think before you act. Only download apps you trust. Keep your phone and apps updated. Use strong passwords and extra security when you can. Remember, safety is in your hands. Don’t hesitate to ask for help with app security. For more mobile app security tips, feel free to contact us today. Article used with permission from The Technology Press.

In the rapidly evolving digital landscape, businesses are increasingly looking to cloud migration as a strategic move to unlock growth and streamline operations. Cloud migration offers numerous advantages, starting with cost savings. By migrating to the cloud, businesses can reduce IT infrastructure costs, as there is no need for physical hardware or maintenance. This shift allows for capital to be reallocated to other critical areas. Additionally, the cloud provides unparalleled scalability. As your business grows, your cloud infrastructure can seamlessly expand to meet increasing demands without requiring substantial upfront investments. Another significant benefit is accessibility. Cloud services enable employees to access data and applications from anywhere, promoting flexibility and collaboration. This not only boosts productivity but also allows businesses to adapt to remote work setups with ease. With enhanced disaster recovery and data security features, the cloud also offers increased resilience against data loss, ensuring business continuity. Through cloud migration, businesses are better positioned to innovate, react swiftly to market changes, and achieve a competitive edge.

In today’s fast-paced digital landscape, the IT infrastructure of a business is not just about hardware and software. It extends to include cloud services, cybersecurity measures, data management, and more. This complexity poses a significant challenge for many businesses, especially small and medium-sized enterprises that may lack the resources to manage it effectively. As technology evolves, the demands of maintaining secure and efficient IT systems grow. Businesses must contend with a host of tasks such as ensuring reliable network connectivity, protecting against cyber threats, all while maintaining compliance with relevant industry regulations. It becomes clear that without a dedicated, skilled IT team, managing these tasks can be overwhelming. This is where outsourcing IT infrastructure management becomes invaluable. By entrusting your IT needs to a professional service provider, you can focus on your core business activities, while ensuring your IT systems are in capable hands. This partnership allows for continuous updates and innovations, ensuring that your business remains competitive and secure in the ever-evolving digital world.

Malware and ransomware are two types of bad software. They can damage your computer or steal your data. Downloading this harmful software comes with serious consequences. In 2024, there were more than 60 million new strains of malware found on the internet. This is why it’s critical to understand the difference between them. This article will help you understand both types of threats. What is Malware? Malware is a general term that means "malicious software." It includes many types of harmful programs. Depending on the type, malware can do different bad things to your computer. These are the four main types of malware: Viruses : These spread from one computer to another. Worms : They can copy themselves without your help. Trojans : They trick you into thinking they're good programs. Spyware : This type watches what you do on your computer. Malware can cause a lot of problems. If you get malware on your device, it can: Slow down your computer Delete your files Steal your personal info Use your computer to attack others What is Ransomware? Ransomware is a type of malware. It locks your files or your entire computer. Then it demands money to unlock them. It is a form of digital kidnapping of your data. Ransomware goes by a pretty basic pattern: 1. It infects your computer, normally through an e-mail or download. 2. It encrypts your files. This means it locks them with a secret code. 3. It displays a message. The message requests money to decrypt your files. 4. You may be provided with a key to unlock the files if you pay. In other cases, the attackers abscond with your money. As of 2024, the average ransom was $2.73 million . This is almost a $1 million increase from the previous year according to Sophos. There are primarily two types of ransomware: 1. Locker ransomware: This locks the whole computer. 2. Crypto ransomware: This only encrypts your files. How are Malware and Ransomware Different? The main difference between malware and ransomware is their goal. Malware wants to cause damage or steal info. Ransomware wants to get money from you directly. While malware wants to take your data, ransomware will lock your files and demand payment to unlock them. Their methods are also different. Malware works in secret and you may not know it’s there. Ransomware makes its presence known so the attackers can ask you for money. How Does It Get Onto Your Computer? Malware and ransomware can end up on your computer in many of the same ways. These include: Through email attachments Via phony websites Via a USB drive with an infection From using outdated software These are the most common methods, but new techniques are on the rise. Fileless malware was expected to grow 65% in 2024 , and AI-assisted malware may make up 20% of strains in 2025. If you get infected by malware or ransomware, it’s important to act quickly. You should know these signs of infection to protect yourself. For malware: Your computer is slow Strange pop-ups appear Programs crash often For ransomware: You can't open your files You see a ransom note on your screen Your desktop background changes to a warning How Can You Protect Yourself? You can take steps to stay safe from both malware and ransomware. First, here are some general safety tips for malware and ransomware: Keep your software up to date Use strong passwords Don't click on strange links or attachments Backup your files regularly For malware specifically, you can protect yourself by using anti-virus programs and being selective with what you download. To stay safe from ransomware, take offline backups of your files and use ransomware-specific protection tools. What to Do If You’re Attacked If you suspect that you have malware or ransomware, take action right away. For Malware: 1. Go offline 2. Run full anti-virus 3. Delete infected files 4. Change all your passwords For Ransomware: 1. Go offline 2. Don't pay the ransom (it may not work) 3. Report the attack to the police 4. Restore your files from a backup Why It Pays to Know the Difference Knowing the difference between malware and ransomware can help with better protection. This will help you respond in the best way when attacked. The more you know what you are against, the better your chance at taking the right steps to keep yourself safe. If you are under attack, knowing what type of threat it is helps you take quicker action. You can take proper steps towards rectifying the problem and keeping your data safe. Stay Safe in the Digital World The digital world can be hazardous. But you can keep safe if you’re careful. Keep in mind the differences between malware and ransomware, and practice good safety habits daily. And, if you are in need of help to keep yourself safe on the internet, never hesitate to ask for assistance. For further information on ensuring that cybersecurity is at the forefront of your business, schedule a discovery call . We want to help keep you secure in the face of all types of cyber threats. Article used with permission from The Technology Press.
In the rapidly evolving digital age, businesses of all sizes face an increasing array of cyber threats. These threats are becoming more sophisticated, making it essential for businesses to continually adapt their cybersecurity strategies. Cyber threats can manifest in many forms, including malware, phishing attacks, ransomware, and data breaches, each capable of causing significant harm to an organization's reputation and bottom line. The impact of a cyber attack can be devastating, leading to financial losses, operational disruptions, and loss of customer trust. Understanding the variety and severity of these threats is the first step in crafting a robust defense. Businesses must stay informed about the latest trends in cybercrime and invest in proactive measures to safeguard their data and IT infrastructure. Additionally, as businesses increasingly adopt remote work practices and digital transactions, there is an added complexity to managing cybersecurity. These changes necessitate a comprehensive approach to cybersecurity that addresses both infrastructure security and the human aspect—ensuring employees are well-trained to recognize and respond to potential threats.




